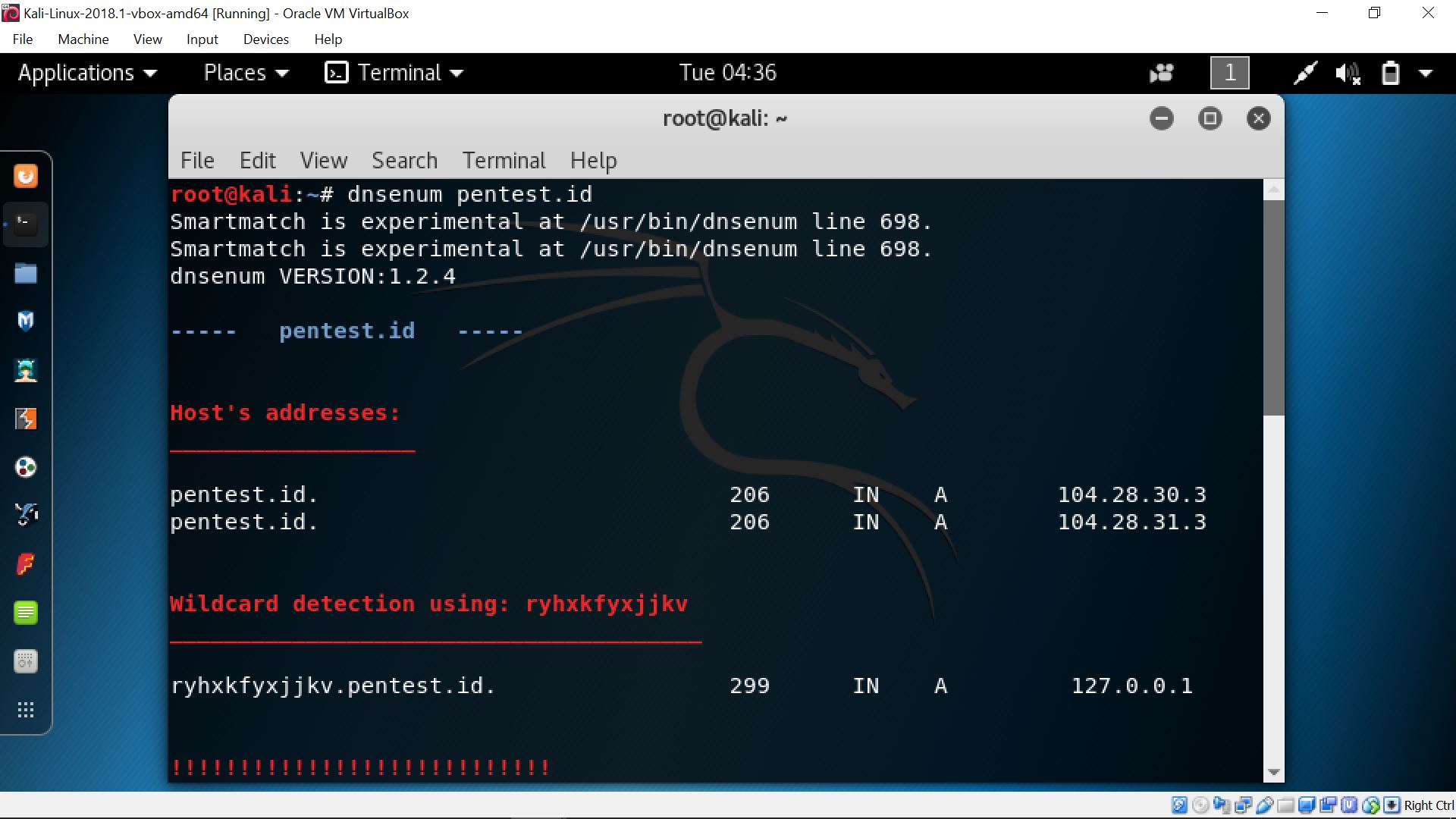
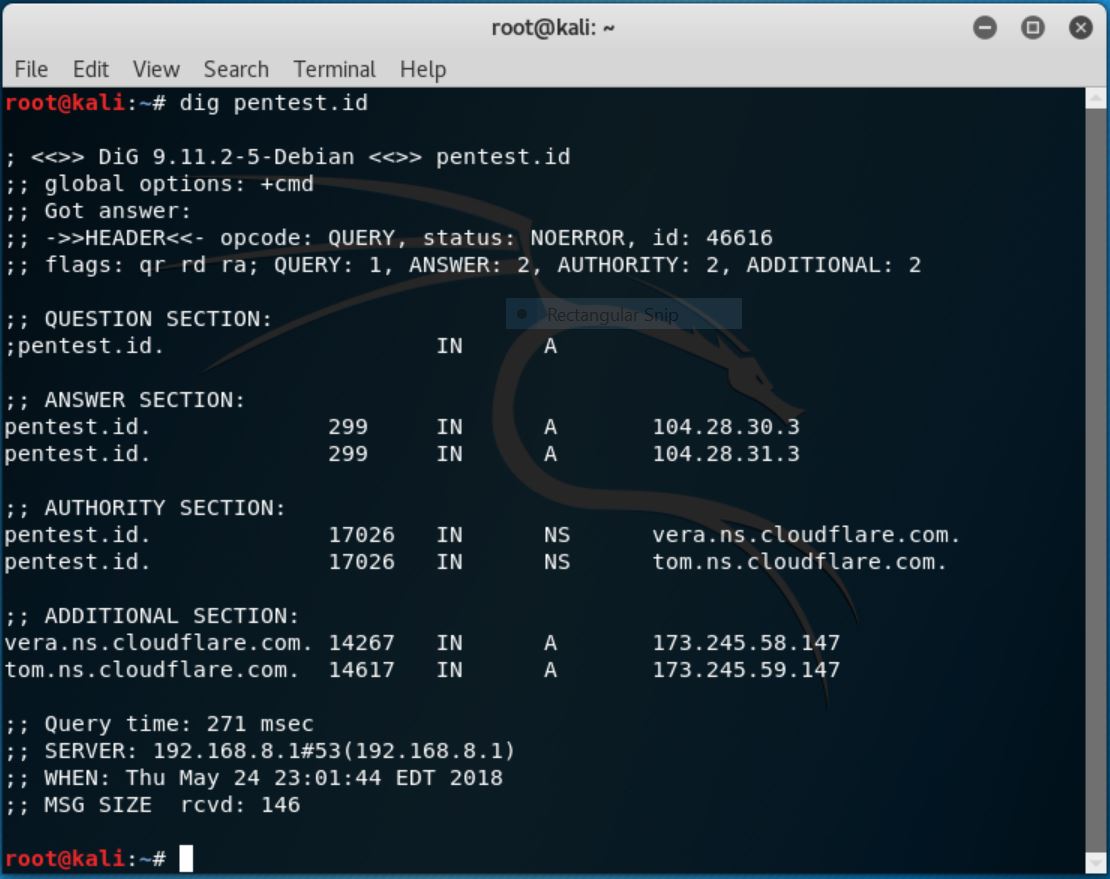
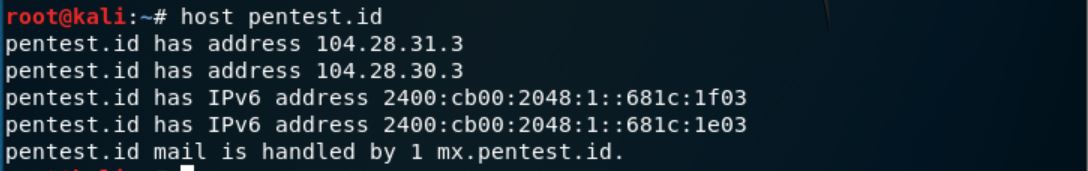
In this session, we continued the previous slide with the explanation about Domain Name Service (DNS) and how it works and how are they vulnerable. With the help of command prompt in Paros Proxy, we can explore the DNS zone transfer using commands such as “dnsenum” and “dig”. These zone transfers are further used to obtain network topologies which is useful for analyzing the internal information of a server. There are also several tools which can determine the devices info such as archive.org and alexa.com. Tools such as pipl.com, tineye.com, and sec.gov/edgar/shtml can be used to access information regarding people, image, and public listed companies respectively.
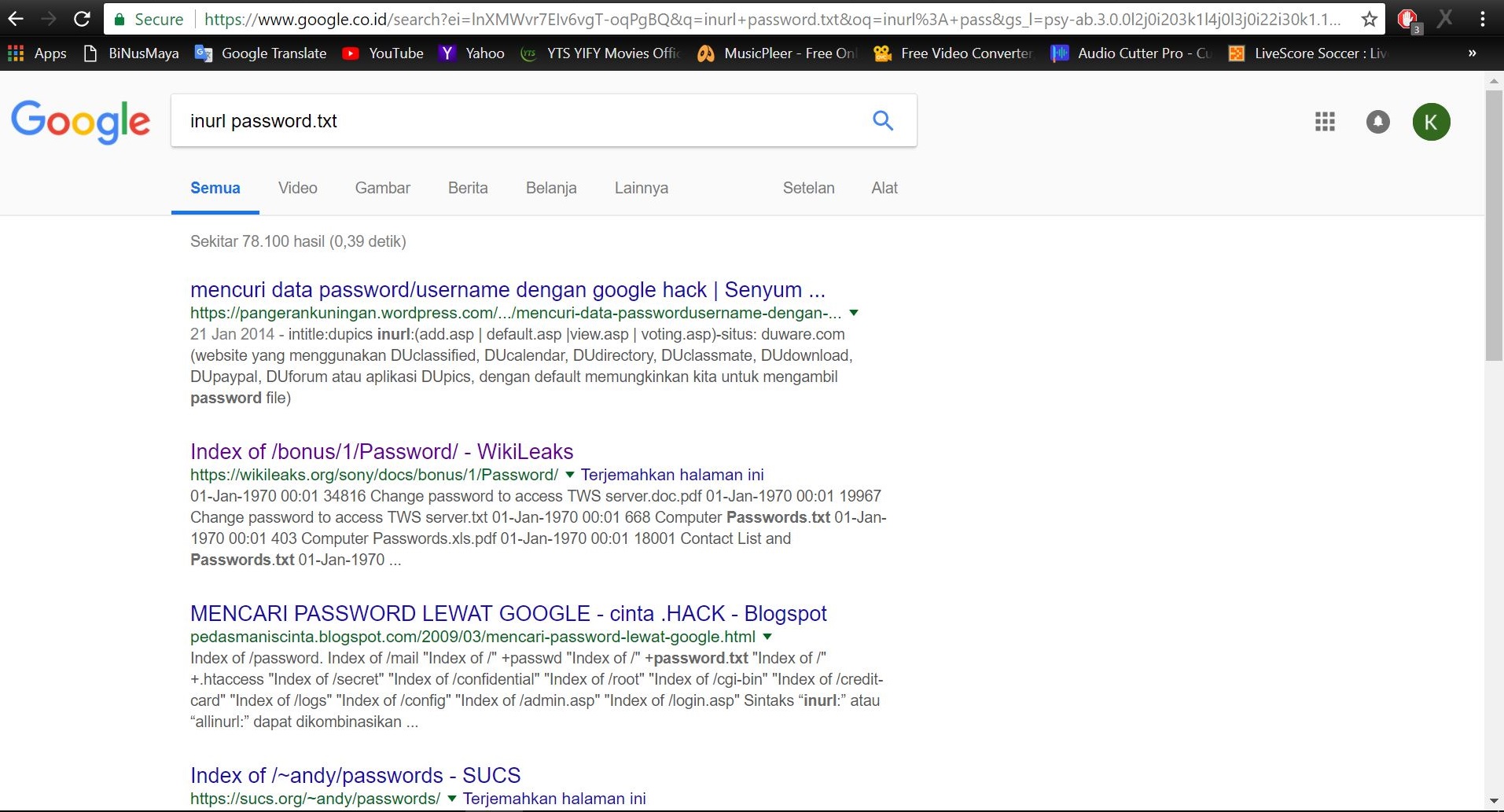
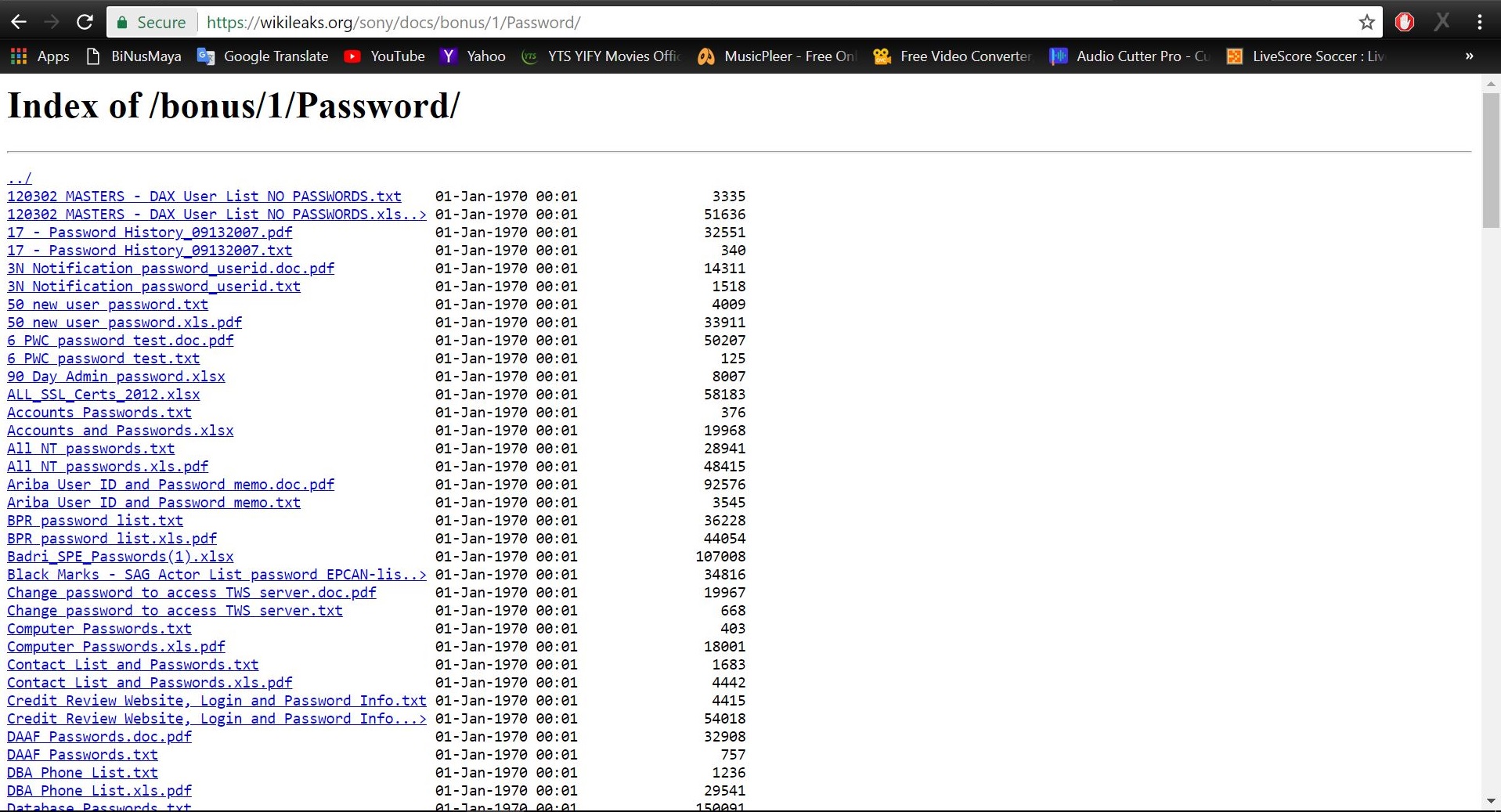
Tools in Kali Linux such as goorecon, theharvester, Maltego can also be used to gather necessary information about the target. We are also taught that Google can also be used for hacking by using certain strings such as “inurl” and “intitle”. Google Hacking Database such as the Google Dorks can be used to extract sensitive documents, information and even passwords which are known to be leaking from their respective servers.
One cannot determine whether their information is safely kept unless they realize that their information is leaked and “roaming around” in the internet. Therefore, there should be an annual check to prevent information leak which can be a threat to the company or organization.
At the end of the session, we are given a quiz which involved gathering information by using Paros Proxy and command prompt to access the information of a certain site.
inurl
dnsenum on pentest.id
dig command
host command
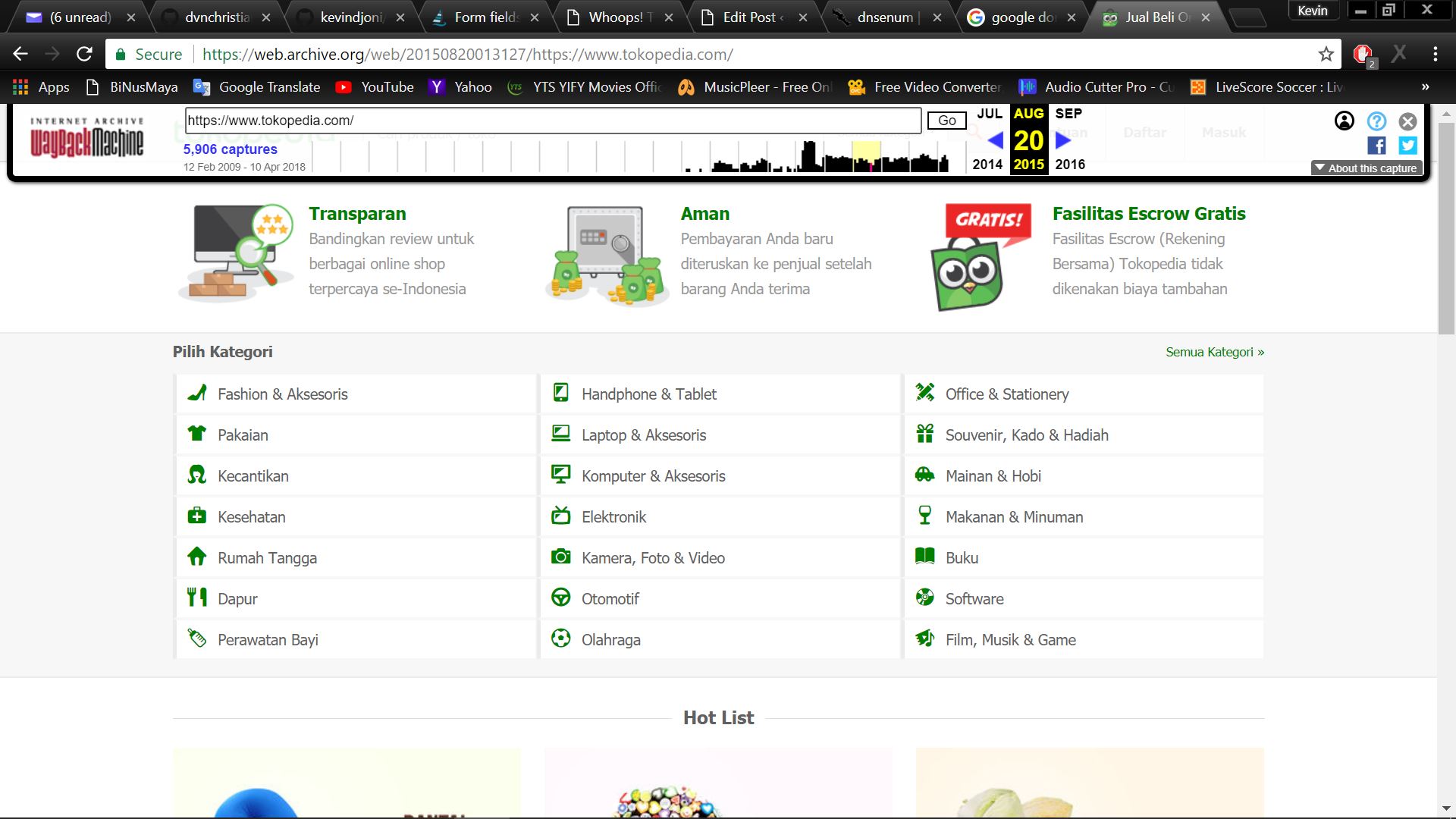
archive.org (display of Tokopedia back in Aug 20th, 2015)