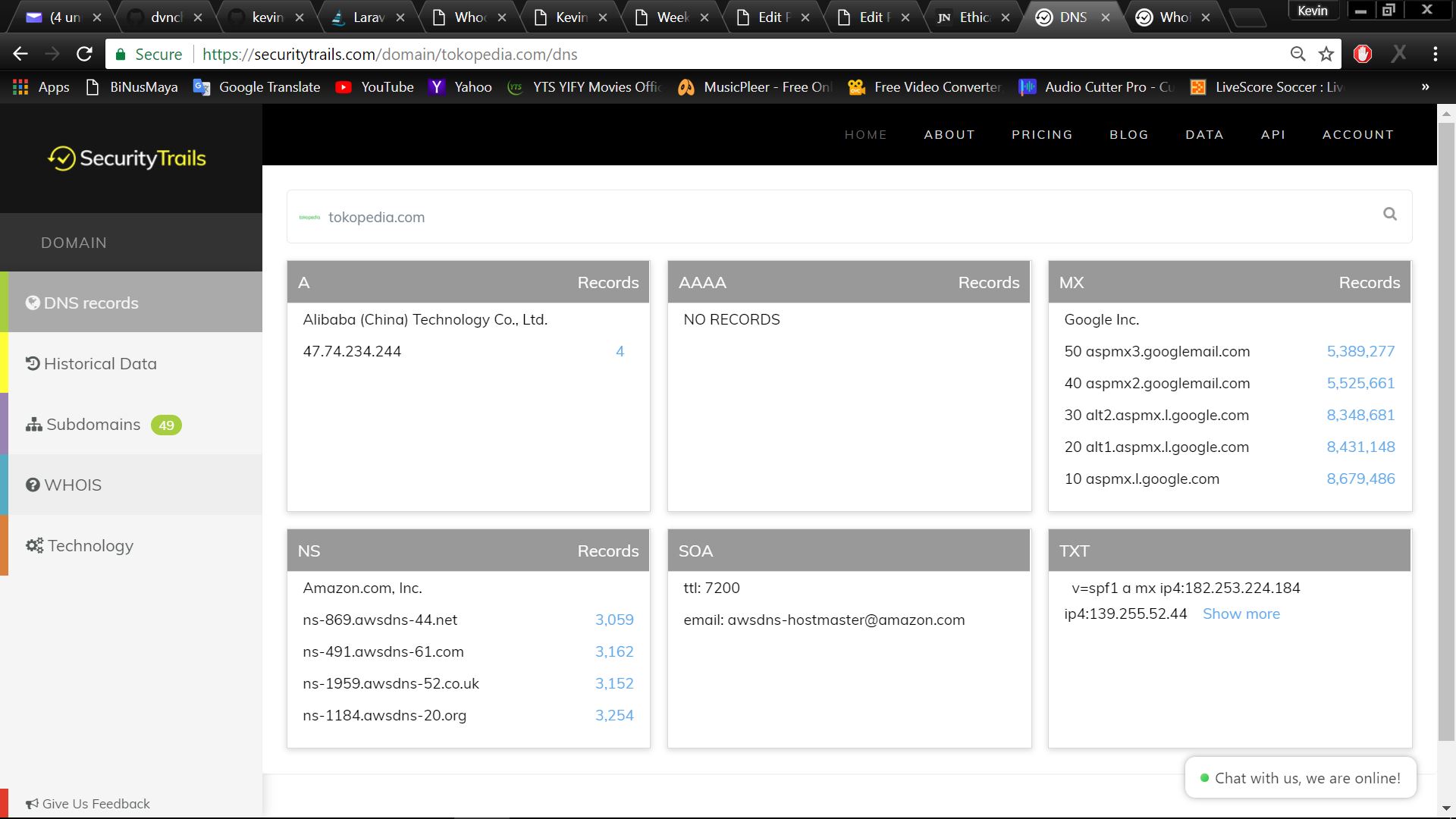
On this week, the session was begun with a trial to retrieve one’s information in the laptop by using a website. One of the students was told to click on a link and to surf it. As a result, some information was retrieved. Then, we are told on how to use dnstrails.com in order to find the old useful information such as the script, admin page, and the server which might be useful if we wish to get the vital information from the website. We were also shown about the old appearance of BiNus’ website as well as the other websites such as tokopedia from archive.org.
One of the most interesting activity in this session is how we could retrieve one’s social media or any information such as his/her username and password by duplicating an exactly same html code in our own server to do so. As the duplicated site resembled the original site, which in this case we used one of the famous internet banking websites, the target will not suspect that they are being targeted for their personal information. Once the target has inserted his/her login information on the given fields, and in order to prevent suspicion from the target, he/she is later redirected to the actual banking website. Therefore, the target will assume that he/she must have inserted the wrong login details which caused him/her to be “redirected” back to the banking site.
To prevent such scam, one must be very careful before clicking on a certain link. Make sure that the given link is exactly the same as the link of your choice. If you ever get a link from someone you both know or not, always recheck that the link that you are about to click is legit. By being careful, you can prevent yourself from getting scammed.
DNSTrails on Tokopedia.com (securitytrails.com)
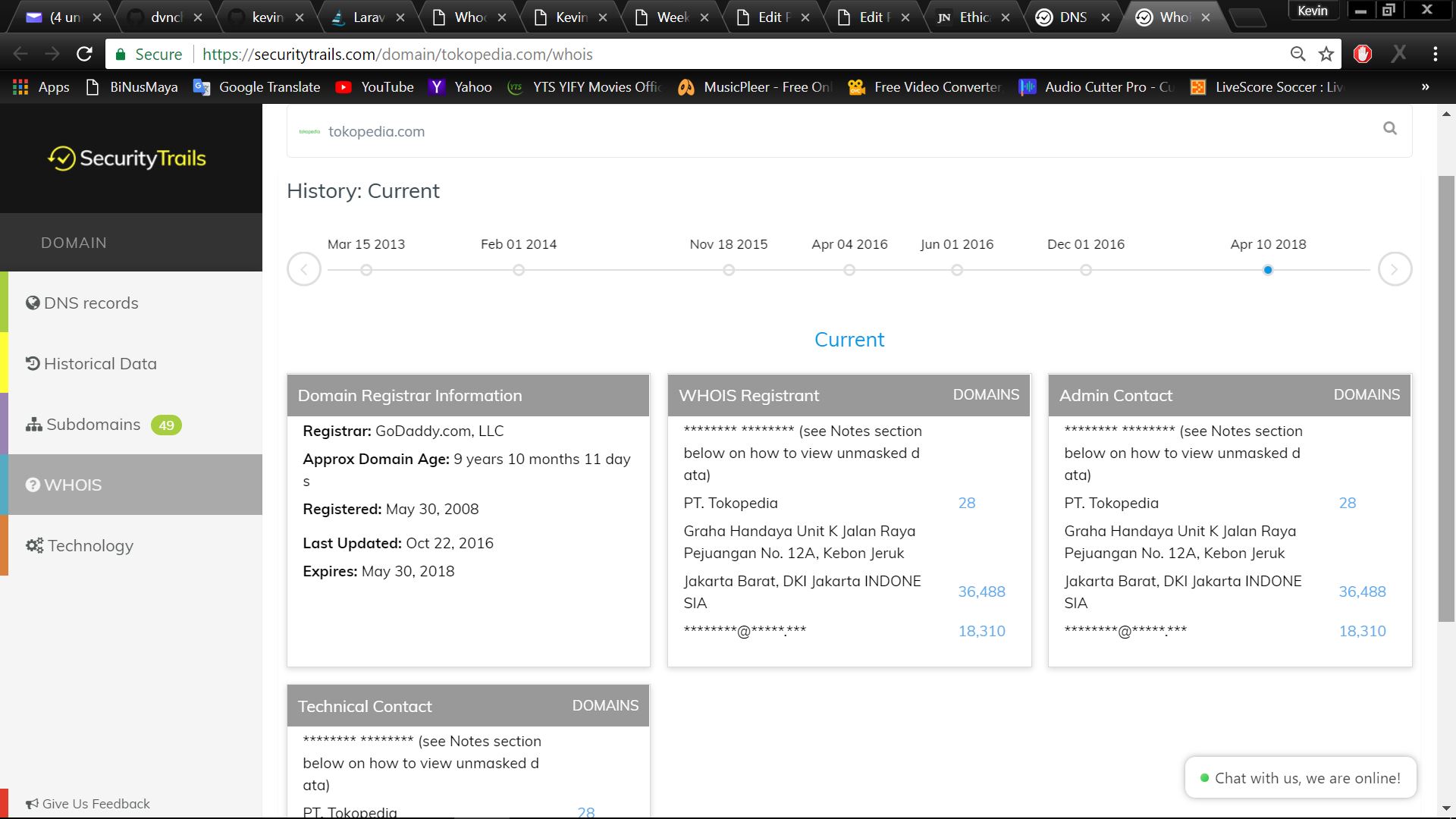
We can also see whois command from securitytrails.com to search the information of tokopedia such as the registar, admin, and etc.