On the second meeting (Week 2), we began our course with the explanation about target scoping. Most of the components in target scoping such as preparing test plan, gathering client information and etc. are checklists for the preparation of penetration testing. Penetration Testing are further divided into different types such as adopting fake identity, investigating employee’s background, and penetrating business partner systems.
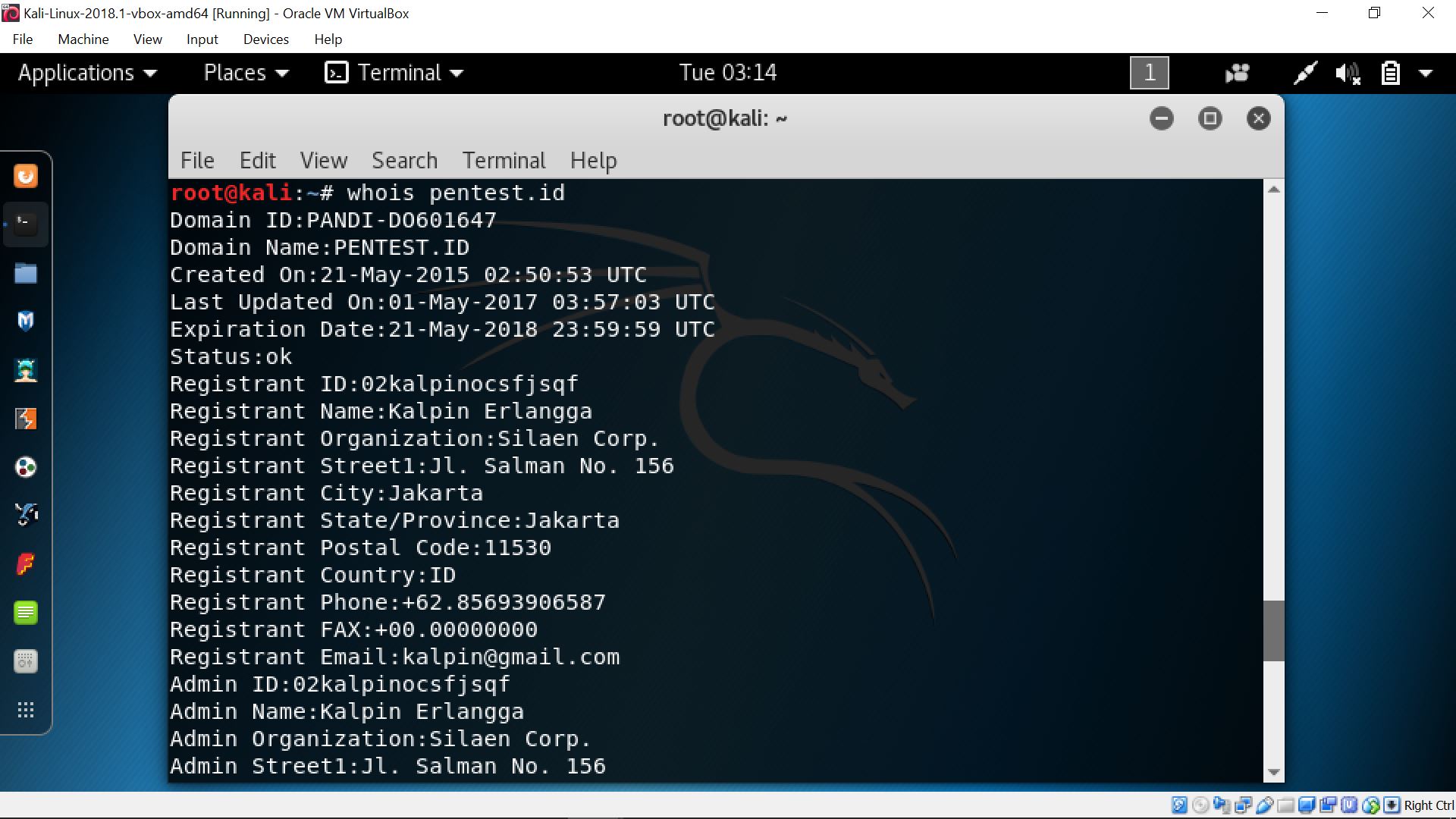
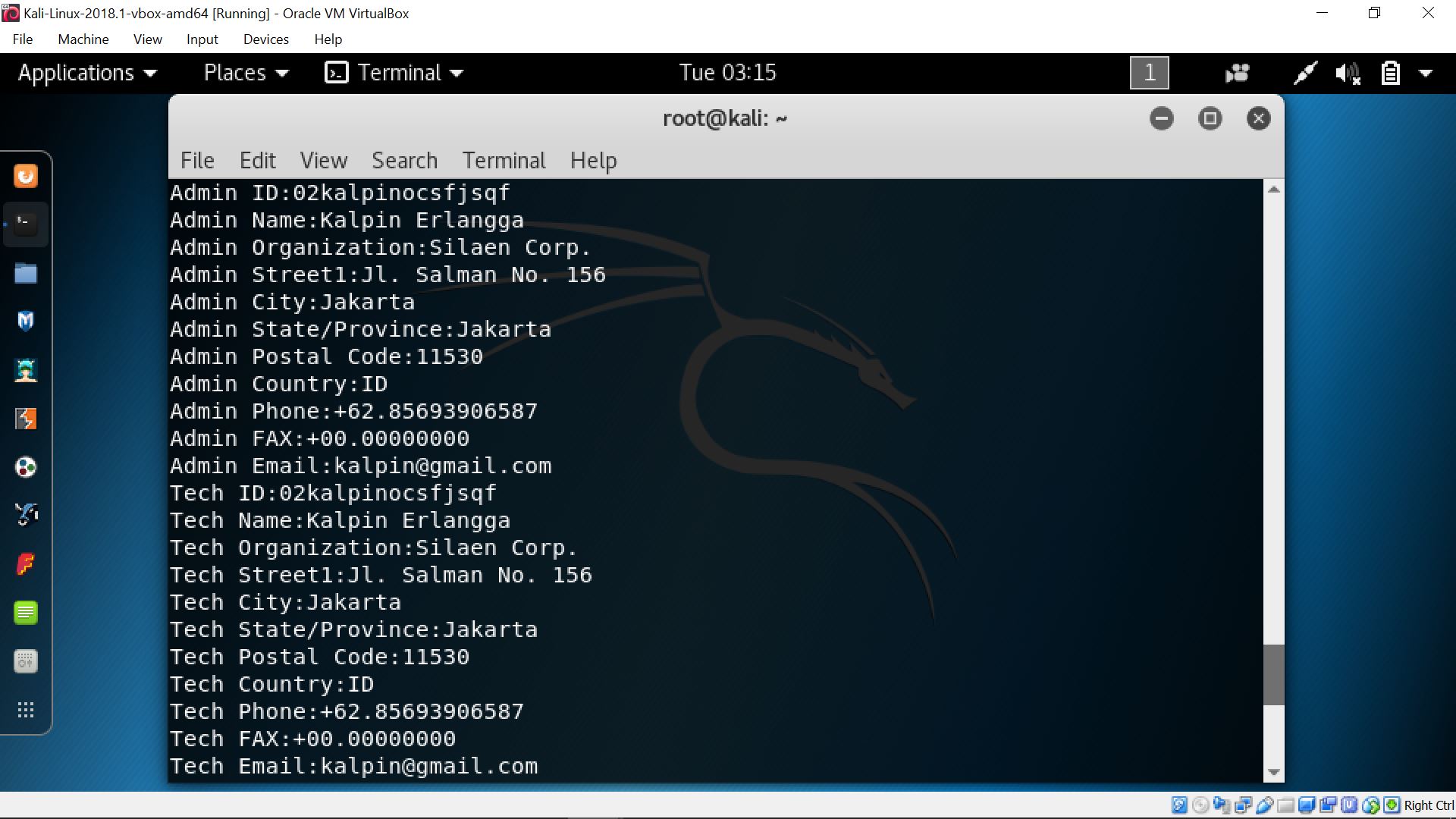
In analyzing a company’s web site, tools such as Paros Proxy can be used. However, some methods of gathering information, involving this Paros Proxy may consume some time. Other Footprinting Tools such as Whois, Host command, SamSpade, and Greenwich can also be used to gather information as well. By the use of Whois, we can reveal the name of the registrant and other important information. E-mail addresses and HTTP Basics are other methods which can also be used to gather information, where E-mail addresses can be used to help retrieve more information compared to previous commands.
whois command on pentest.id (whois pentest.id)