In brief, DVWA or Damn Vulnerable Web Application is a web application whose goal is to provide a place for security professionals or also students like us to practice our skills and tools without having to worry about getting caught by the authorities for conducting an illegal activity.
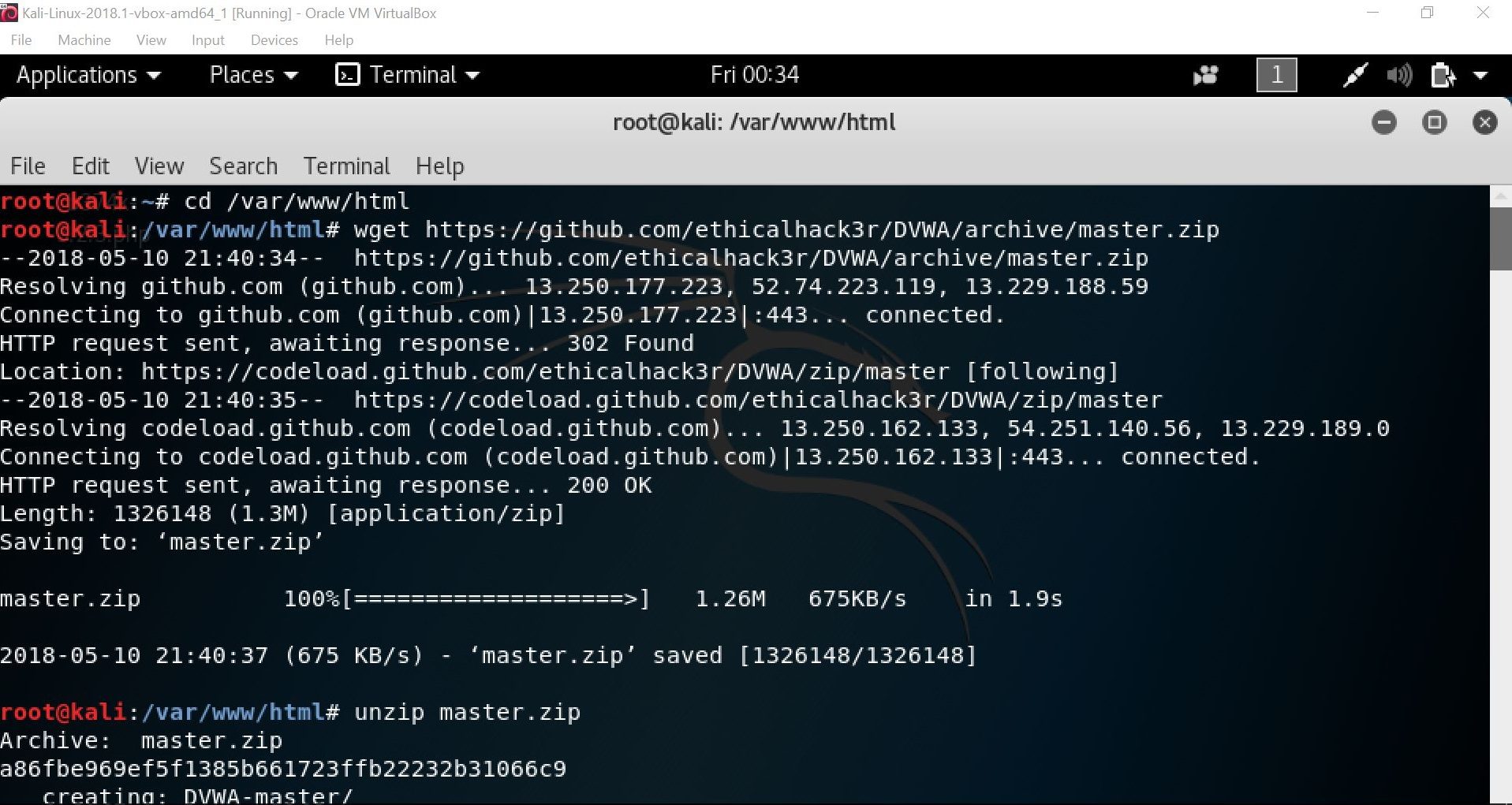
First of all, we need to go to the /var/www/html directory by using the cd command “cd /var/www/html”, followed by a wget command to retrieve a zip file from a github repository and to unzip the zip file itself.
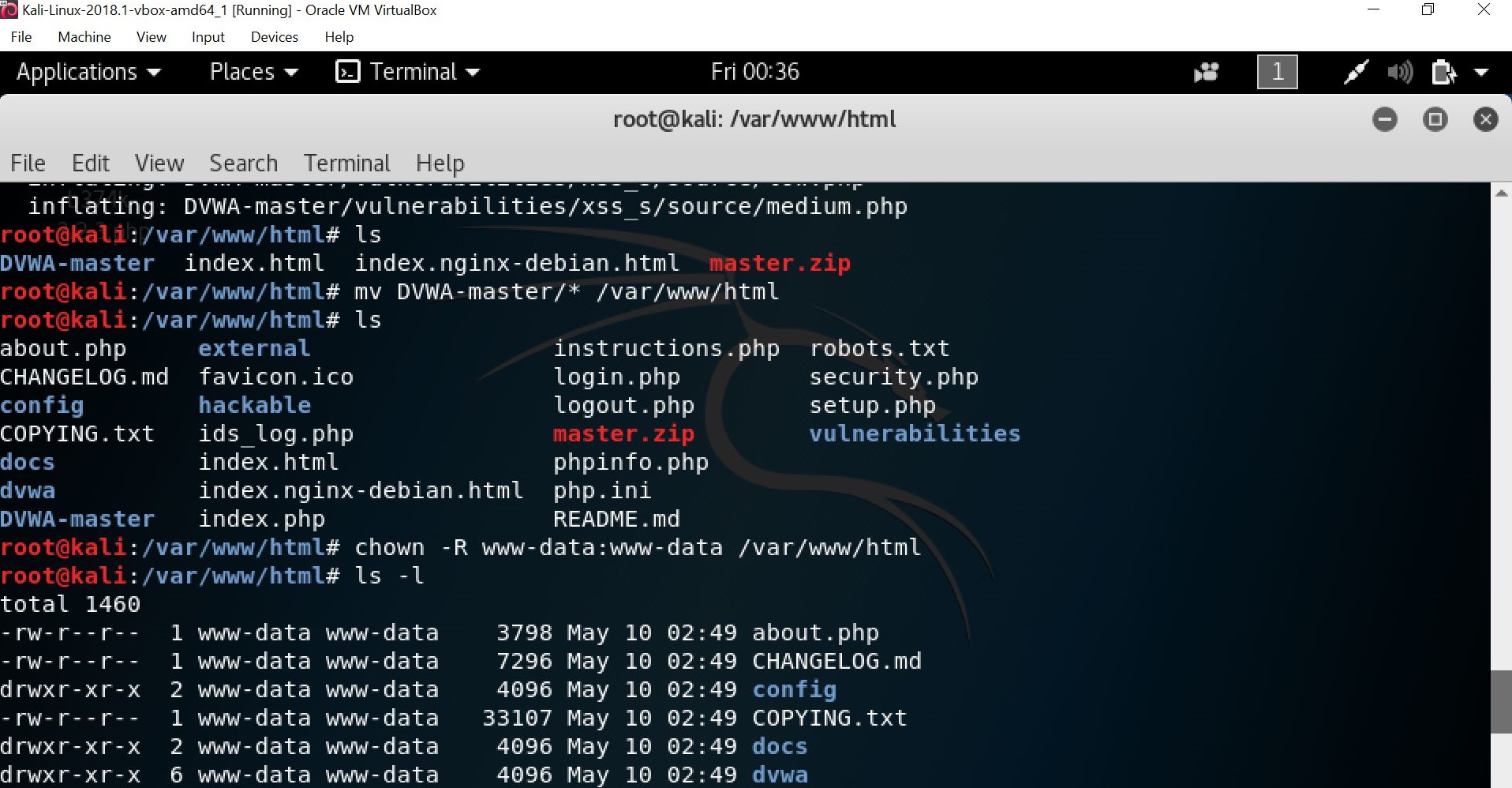
Then, move the DVWA-master file to a root directory by using the “mv DVWA-master/* /var/www/html”. Once we have moved the file, change the owner the /var/www/html directory by typing the chown (change owner) command as such “chown -R www-data:www-data /var/www/html”.
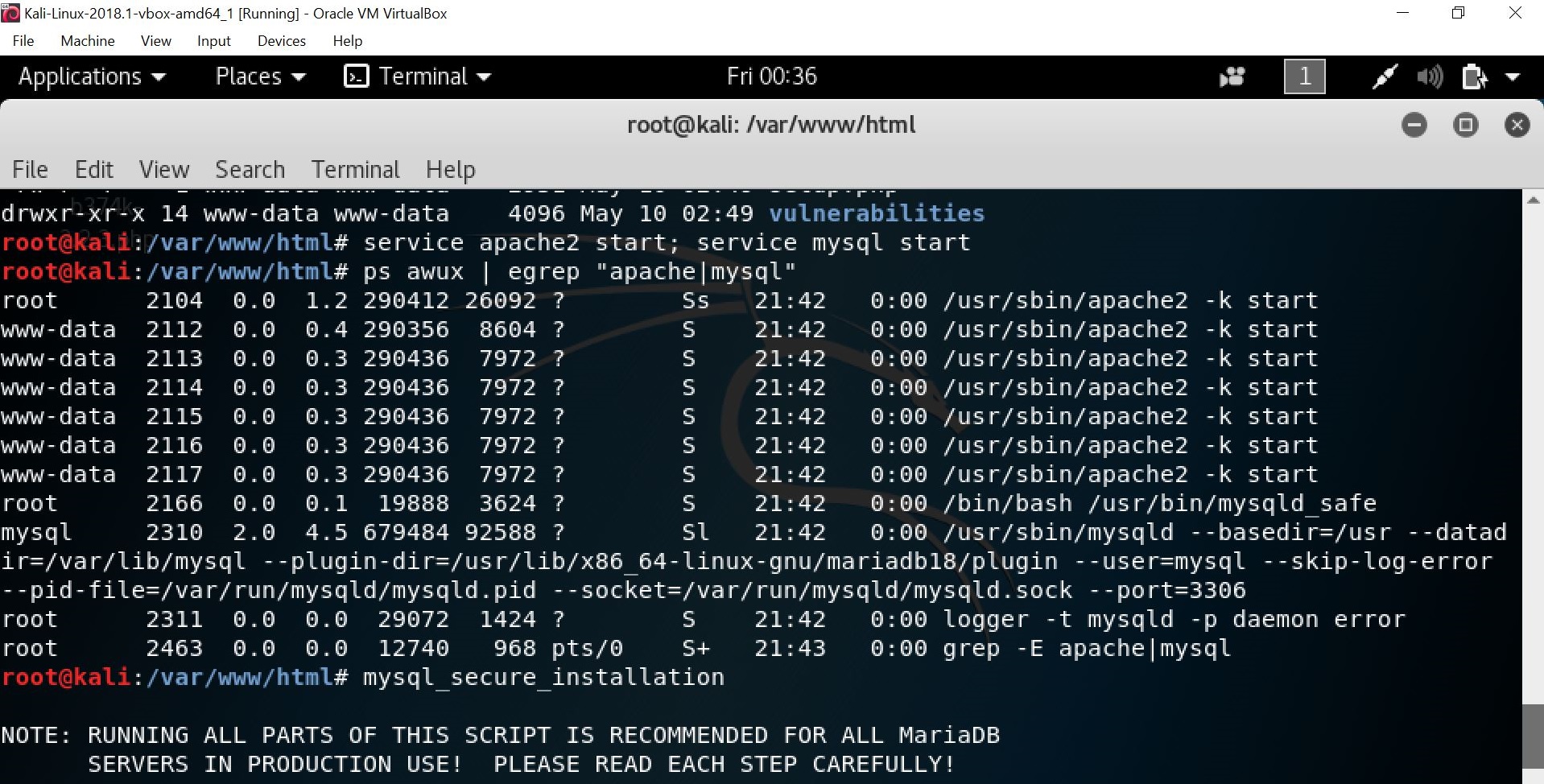
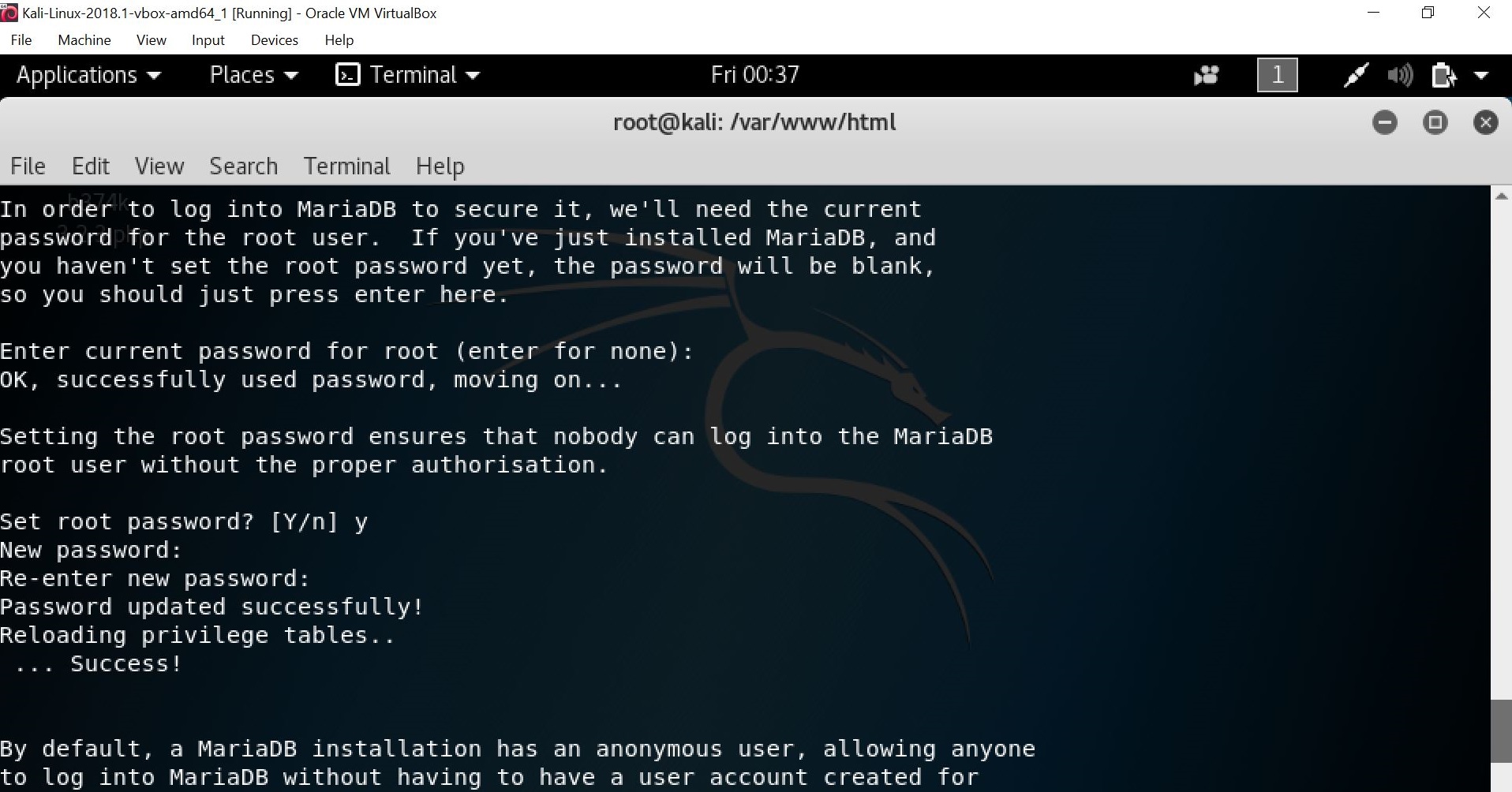
Then, the apache and MySQL services should be set first by using the “service apache2 start: service mysql start” and “ps awux | egrep “apache|mysql”” command. Once completing setting the services, secure the MySQL installation by using the “mysql_secure_installation” command.
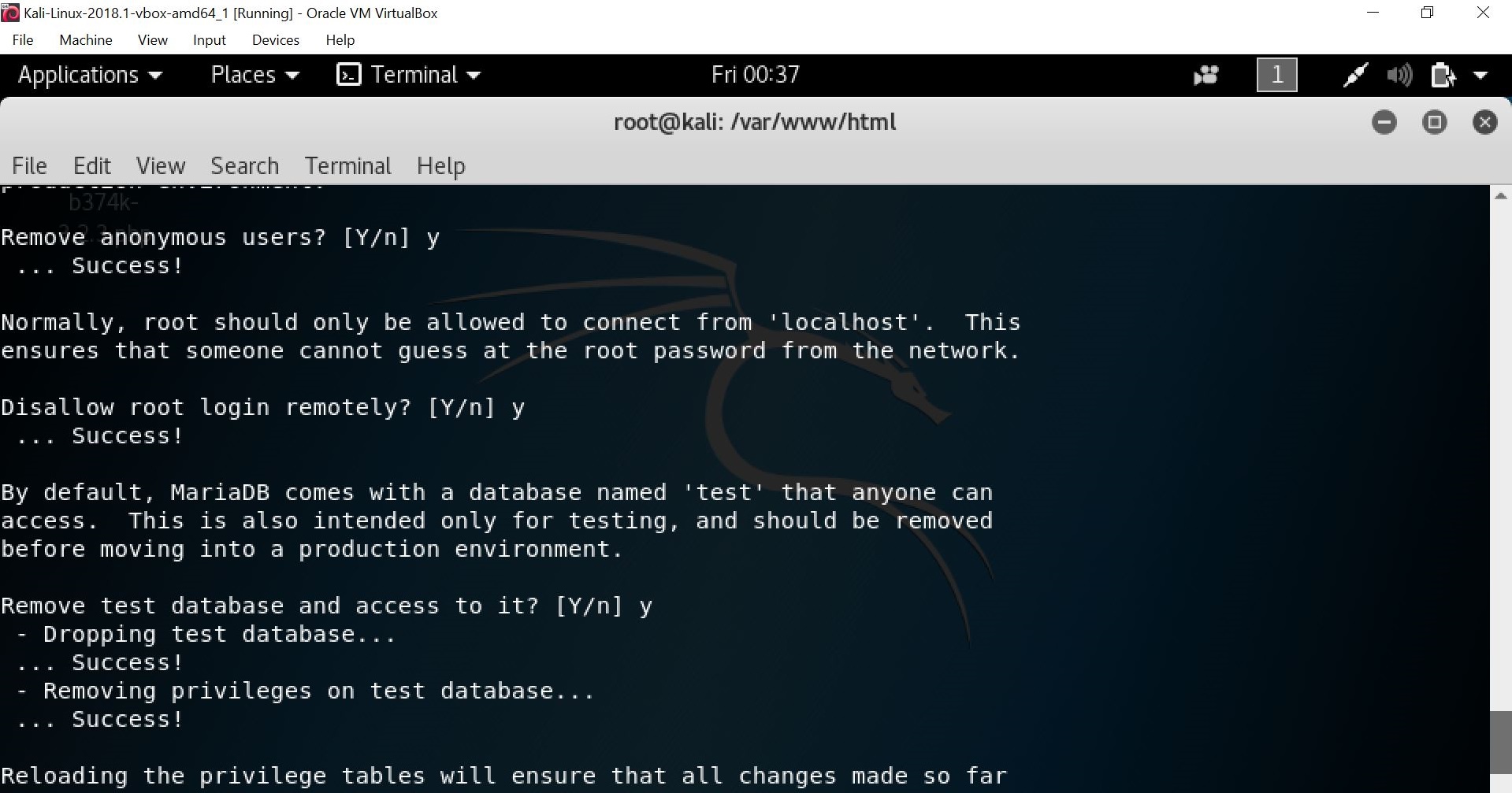
Once typing in the “mysql_secure_installation” command, you will be asked whether the root password wants to be set. Set the root password and type “Y/y” in all fields.
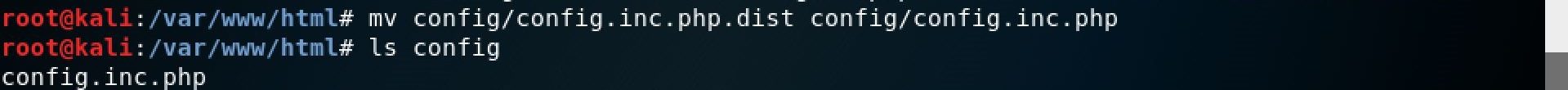
Once completing all the steps in the installation, change the config.inc.php.dist file in config directory to config.inc.php.
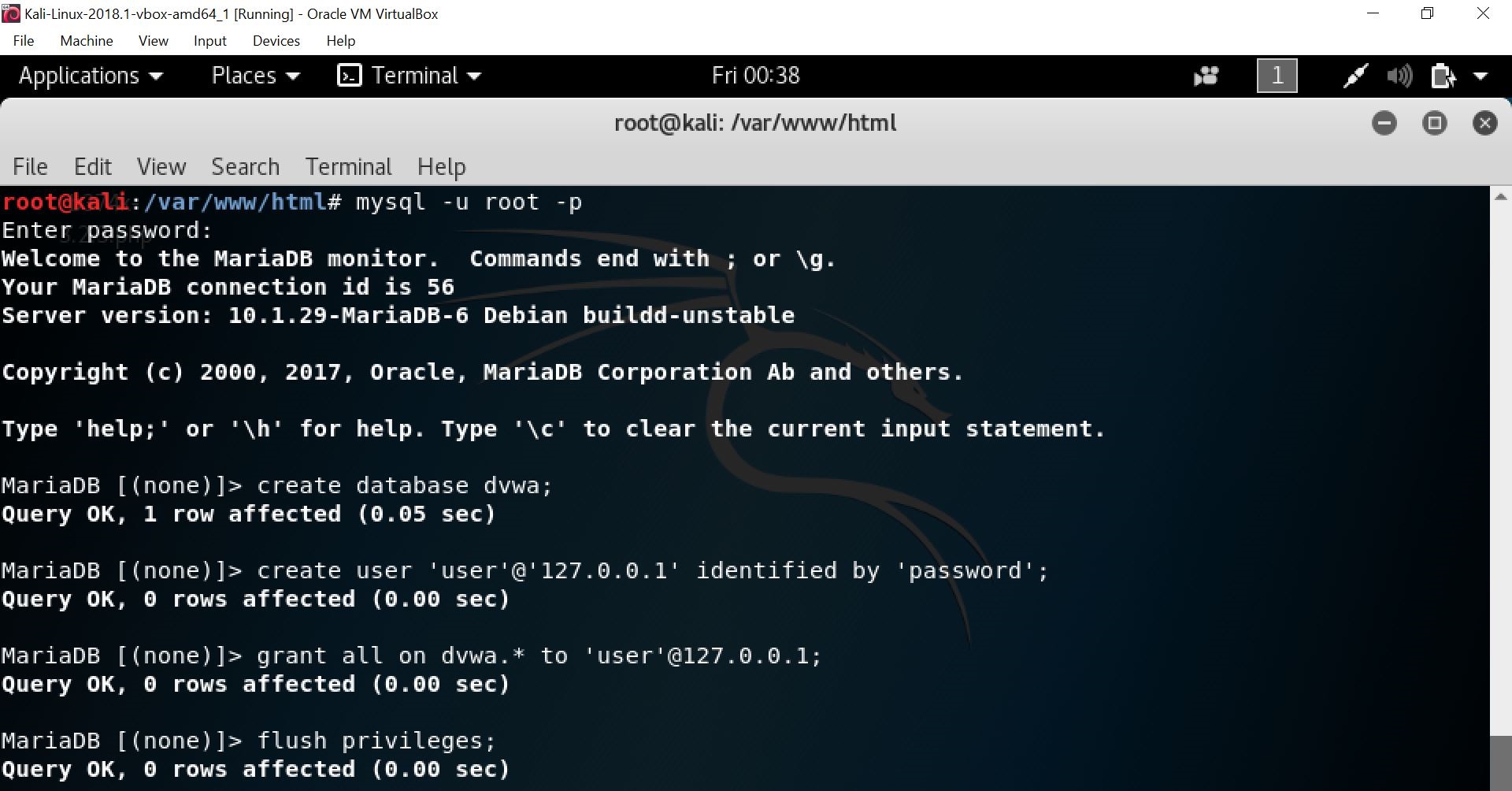
Then, create a database in the terminal by typing the “mysql -u root -p” command, then enter your root password, followed by the query to create the database.
We should edit the config/config.inc.php file by using the “nano config/config.inc.php”.
Change the ‘db_user’ to ‘user’ and ‘db_password’ to the previous root password that you set previously.
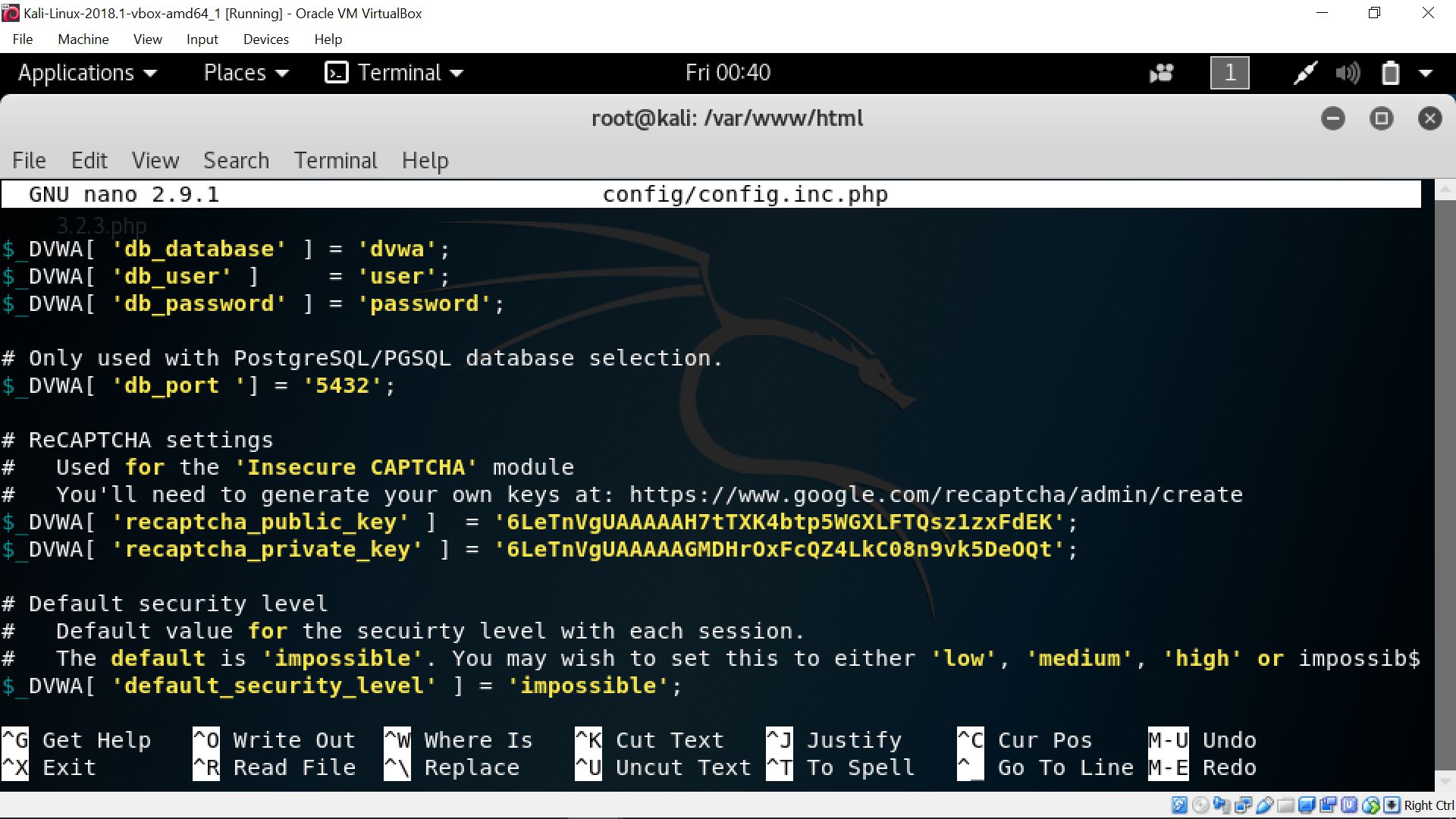
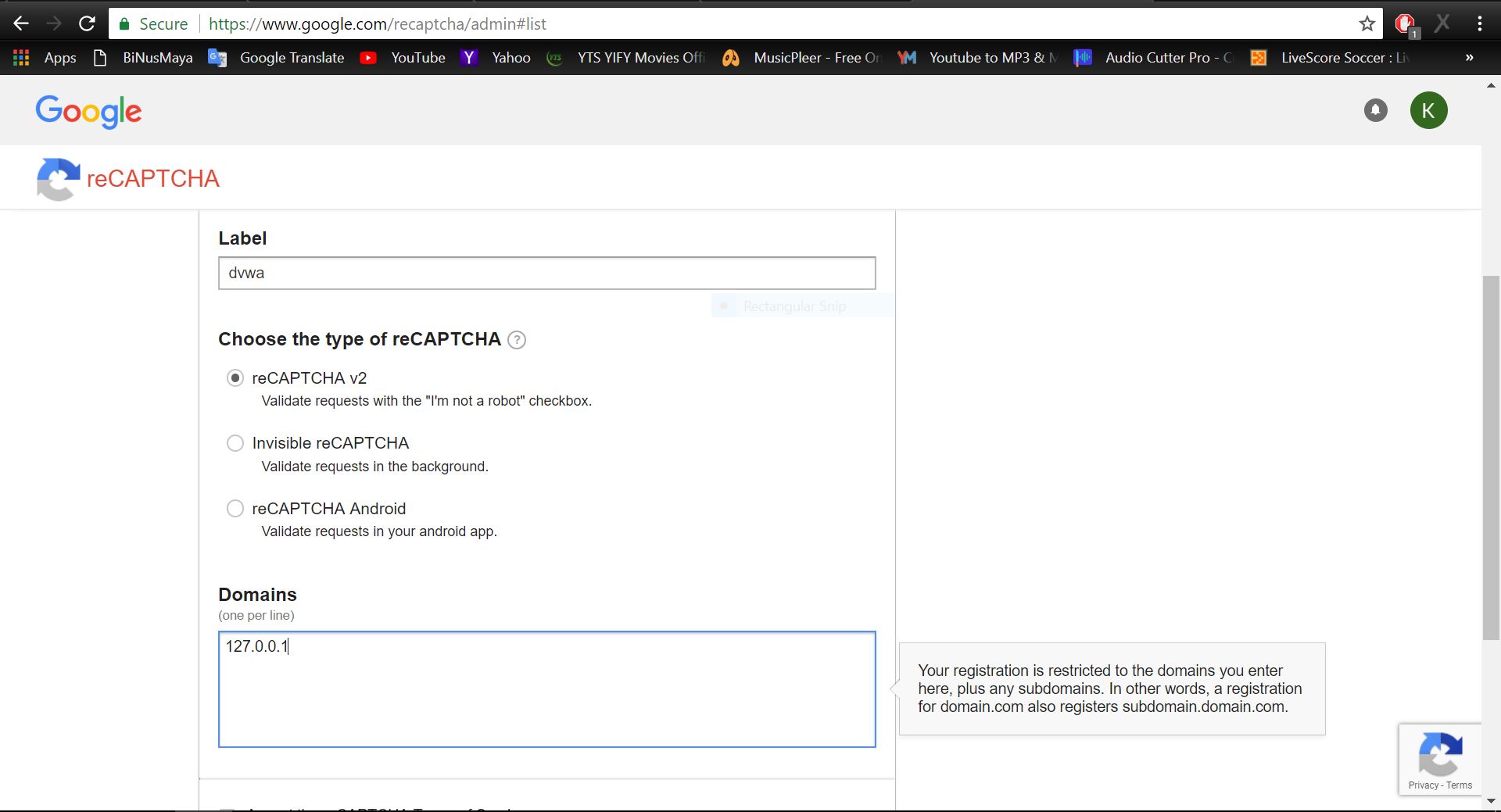
In order to get the reCAPTCHA keys, you can search in google for the keyword “google recaptchca” or you can simply type in the url “https://www.google.com/recaptcha/admin”. Then, type on the label field any name you want to label your reCAPTCHA, followed by selecting the reCAPTCHA v2 and filling the domain with your local ip address like follows.
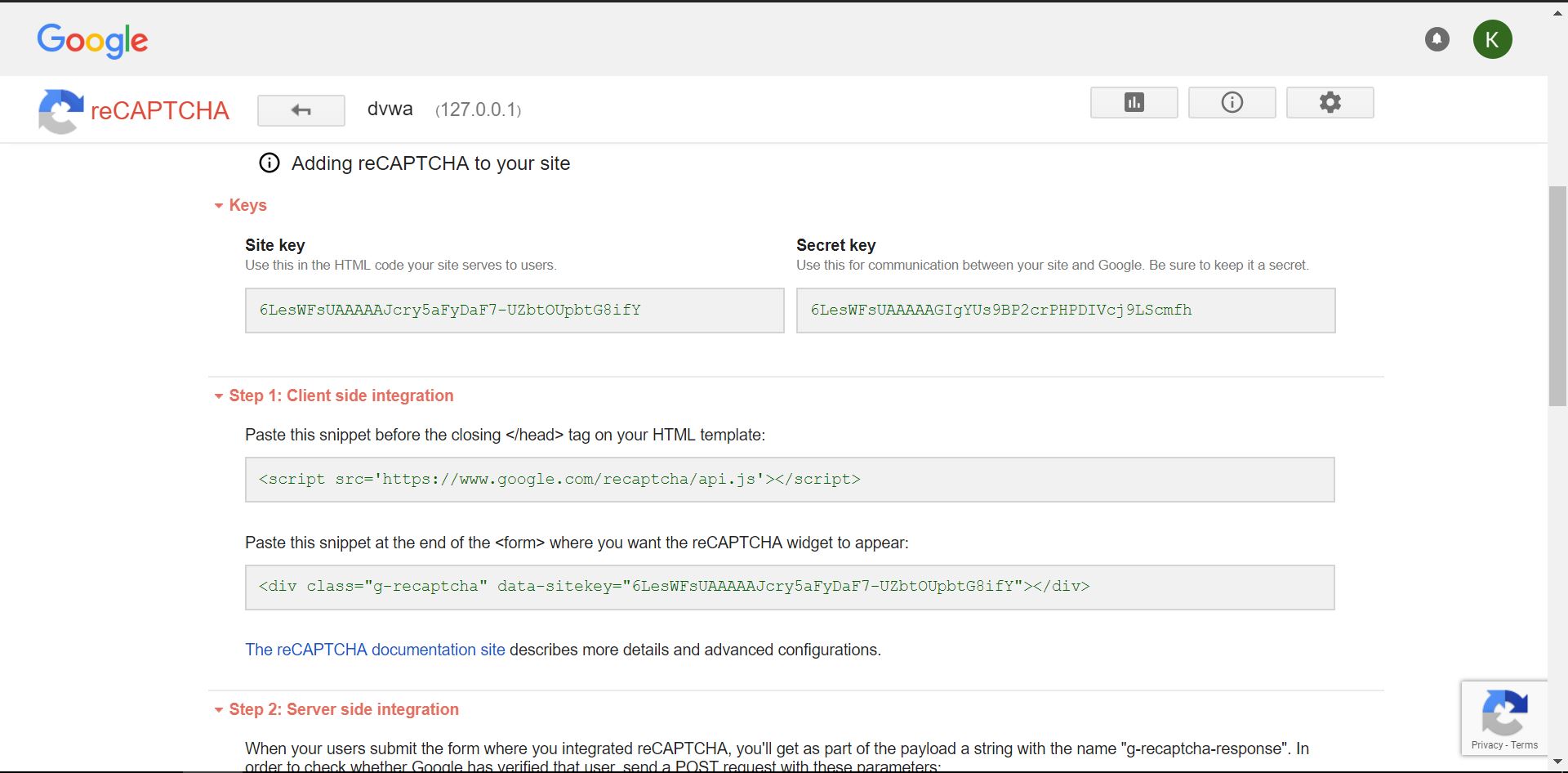
We will get the site key and the secret key which need to be filled in the recaptcha_public_key and recaptcha_private_key.

If we type in our local ip address, which in my case is 127.0.0.1, and the following page is shown, it means that the dvwa installation which we did earlier has succeeded.