In this session, both classes were combined and the topic we learned is about port scanning. Port Scanning is a process which involves scanning of different port in order to find opened ones. The purpose of port scanning is to find vulnerability which can only be found if a port is open. In this process, we should not only scan for only well-known ports (Port 0-1023) but also the Ephemeral Ports (Port 1024+). We can get information regarding which port is open, closed, filtered (Port behind a firewall), and also guesses about which OS is running in the machine. There are some types of scan in port scanning such as:
- SYN Scan: Scan which is not known by the machine.
- Connect Scan: Involving SYN, SYN-ACKnowledge, and ACK.
- NULL Scan: Sending no response.
- FIN Scan: Finish Scan (Terminate Connection).
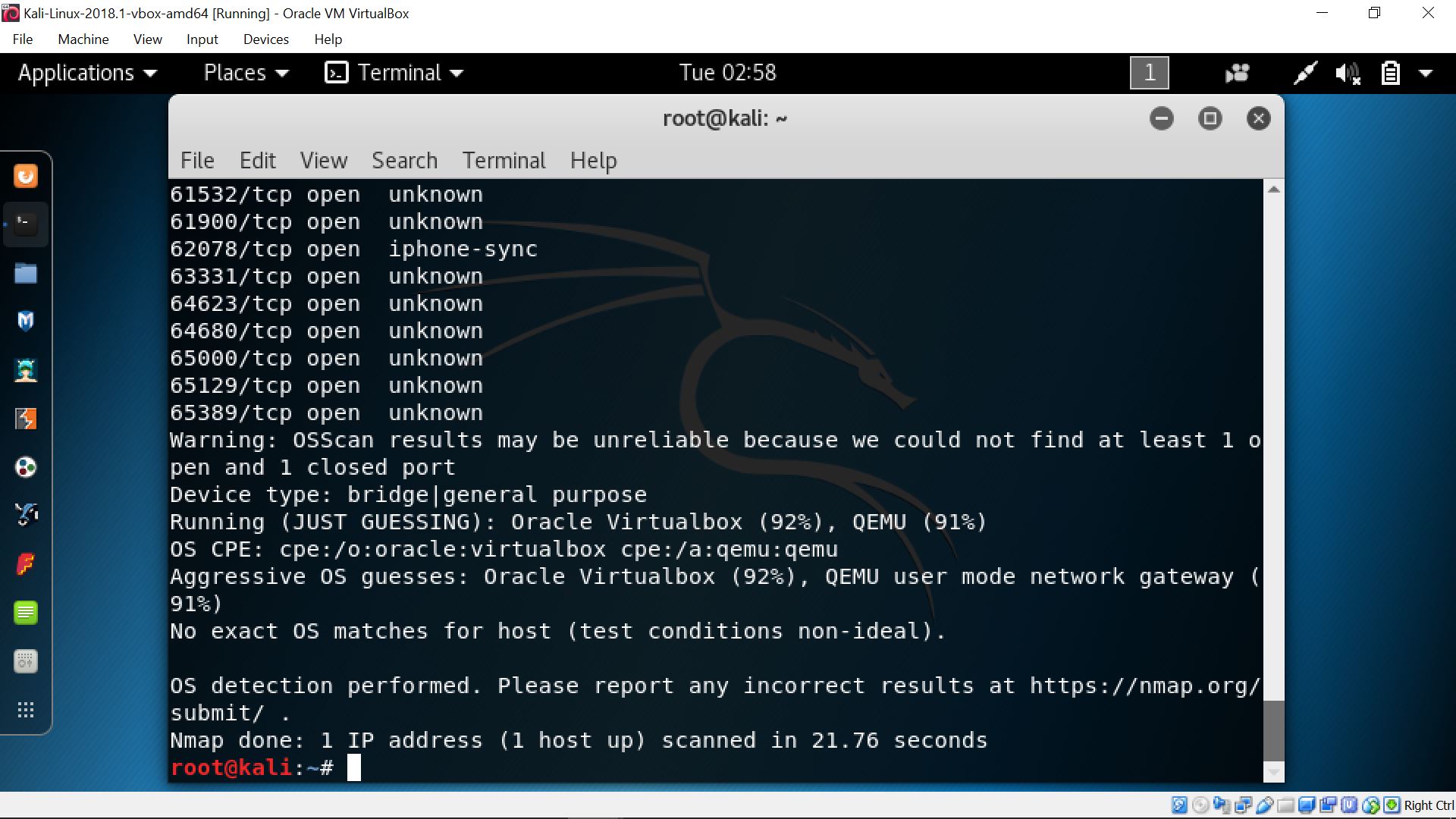
At the end of the session, we conducted a practice on port scanning by using a tool such as the Nmap and Zenmap (GUI version of Nmap) in our Linux Virtual Machine. We were assigned to find the detail services of the 2 given hosts. Firstly, we used bash shell scripting method to look for open port(s) and the best guess about the OS the machine is using. In order to confirm the type of OS the machine is working, we used both Nmap and Zenmap to do so. Other than port scanning, Nmap also add the OS detection capability & provide vulnerability scanning (only if the port is open). In addition, we can also use p0f and nikto (nikto -host). To know what nmap is doing in the virtual machine, you can run nmap and turn on wireshark at the same time to see every packet that nmap is sending.
There are different types of sending packets from T0-T5. Higher the number, faster it will be. However, the reason behind using the T0 is to prevent suspicion which may result in yourself from being blocked as it send only a small number of packets, unlike T4 or T5.
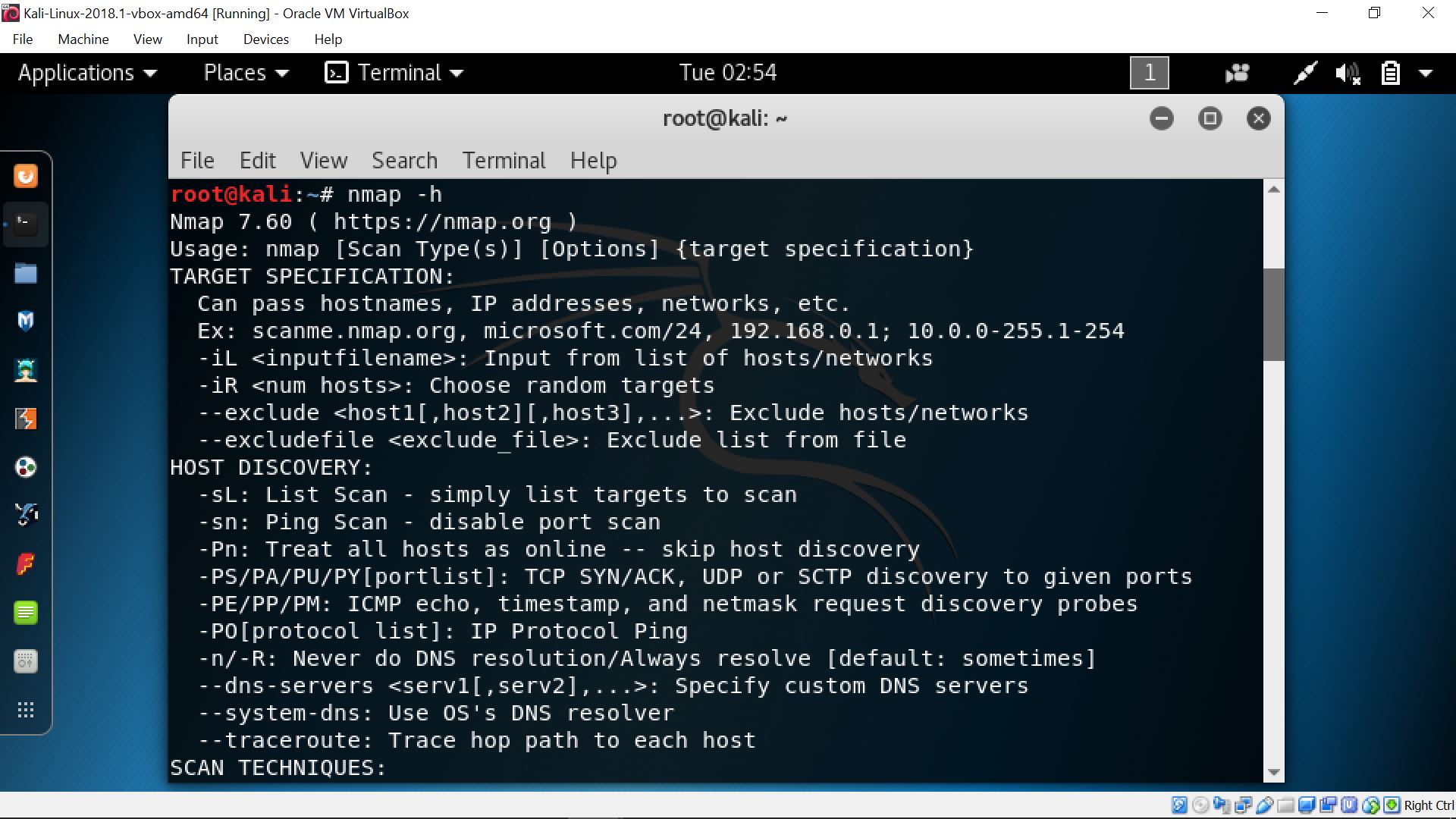
Nmap help command (nmap -h)
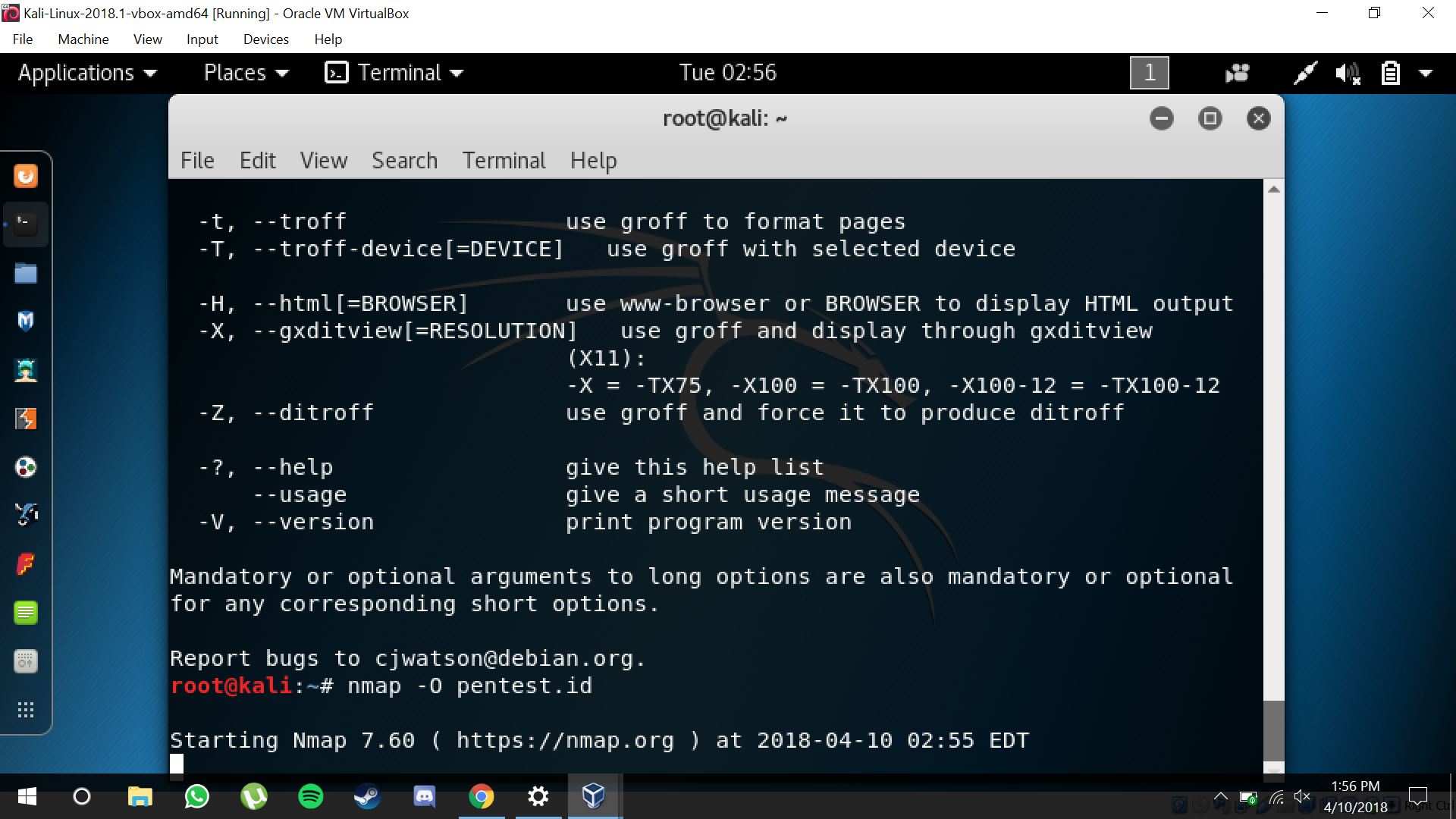
Testing nmap on pentest.id (nmap -O pentest.id)
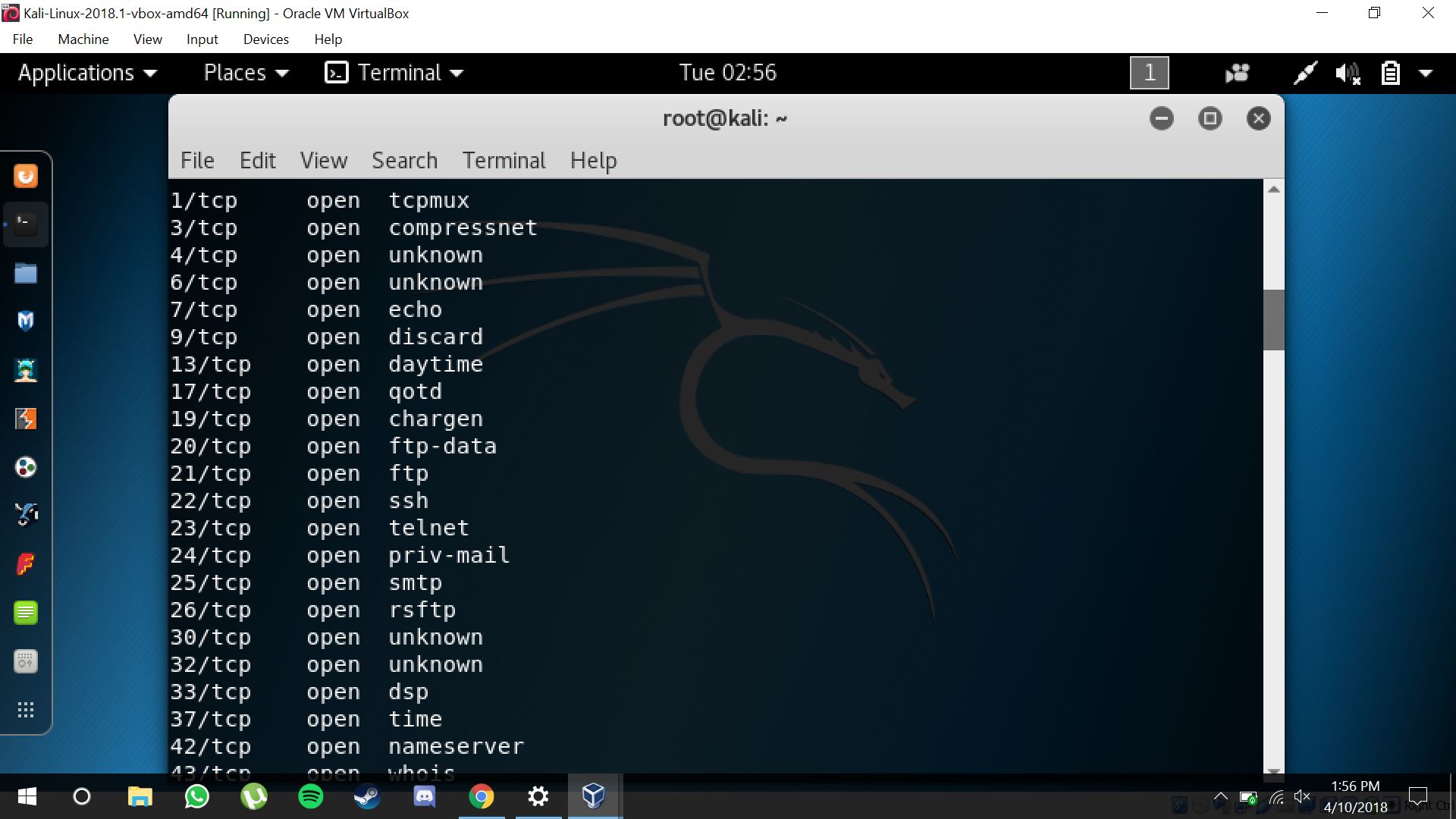
Results of nmapping
nikto (Double check the information)